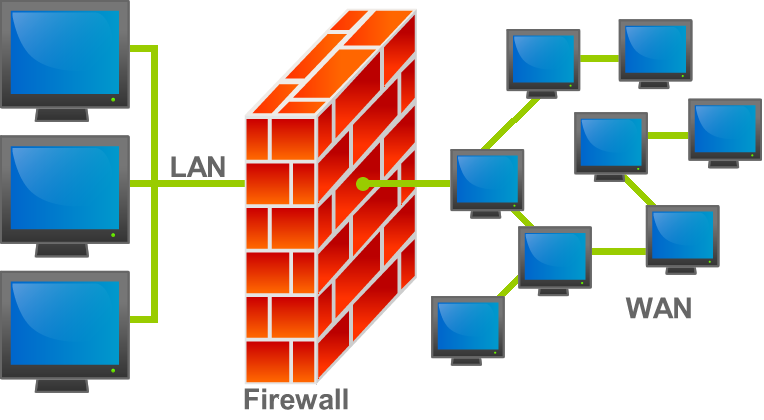
As cybercrime continues to increase and threaten businesses across the world, you probably know that your organization needs firewall security; in fact, you may even already have a firewall management program in place. But what exactly is firewall security, and what does firewall management entail?
The word firewall originally referred literally to a wall, which was
constructed to halt the spread of a fire. In the world of computer
firewall protection, a firewall refers to a network device which blocks
certain kinds of network traffic, forming a barrier between a trusted
and an untrusted network. It is analogous to a physical firewall in the
sense that firewall security attempts to block the spread of computer
attacks.
Packet filtering firewall
This type of firewall has a list of firewall security rules which can block traffic based on IP protocol, IP address and/or port number. Under this firewall management program, all web traffic will be allowed, including web-based attacks. In this situation, you need to have intrusion prevention, in addition to firewall security, in order to differentiate between good web traffic (simple web requests from people browsing your website) and bad web traffic (people attacking your website).
A packet filtering firewall has no way to tell the difference. An additional problem with packet filtering firewalls which are not stateful is that the firewall can’t tell the difference between a legitimate return packet and a packet which pretends to be from an established connection, which means your firewall management system configuration will have to allow both kinds of packets into the network.
Stateful firewall
This is similar to a packet filtering firewall, but it is more intelligent about keeping track of active connections, so you can define firewall management rules such as “only allow packets into the network that are part of an already established outbound connection.” You have solved the established connection issue described above, but you still can’t tell the difference between “good” and “bad” web traffic. You need intrusion prevention to detect and block web attacks.
Deep packet inspection firewall
There are three caveats, however: first, for some vendors, the definition of “deep” extends to some particular depth in the packet and does not necessarily examine the entire packet. This can result in missing some kinds of attacks. Second, depending on the hardware, a firewall may not have adequate processing power to handle the deep packet inspection for your network. Be sure to ask questions about how much bandwidth it can handle while performing such inspection. And finally, embedded firewall management technology may not have the flexibility to handle all attacks.
Application-aware firewall
Similar to deep packet inspection, except that the firewall understands certain protocols and can parse them, so that signatures or rules can specifically address certain fields in the protocol. The flexibility of this approach to computer firewall protection is great and permits the signatures or rules to be both specific and comprehensive. There are no specific drawbacks to this approach to firewall security as generally it will yield improvements over a standard “deep packet inspection” approach. However, some actual attacks may be overlooked (false negatives) because the firewall security parsing routines are not robust enough to handle variations in real-world traffic.
Application proxy firewall
An application proxy acts as an intermediary for certain application traffic (such as HTTP, or web, traffic), intercepting all requests and validating them before passing them along. Again, an application proxy firewall is similar to certain kinds of intrusion prevention. The implementation of a full application proxy is, however, quite difficult, and each proxy can only handle one protocol (e.g. web or incoming email).
For an application proxy firewall to be effective as computer firewall protection, it has to be able to understand the protocol completely and to enforce blocking on violations of the protocol. Because implementations of the protocol being examined often do not follow a protocol correctly, or because implementers add their own extensions to a protocol, this can result in the proxy blocking valid traffic (false positives). Because of these kinds of problems, end users will often not enable these technologies.
As you can see, there are areas of overlap between intrusion prevention and certain types of firewall security. The terminology in this field is still being worked out, so it can be confusing at times.
 Keeping You Safe With Home/Business Security Tips, News and Reviews Keeping You Safe With Home/Business Security Tips, News and Reviews
Keeping You Safe With Home/Business Security Tips, News and Reviews Keeping You Safe With Home/Business Security Tips, News and Reviews